AI Explain
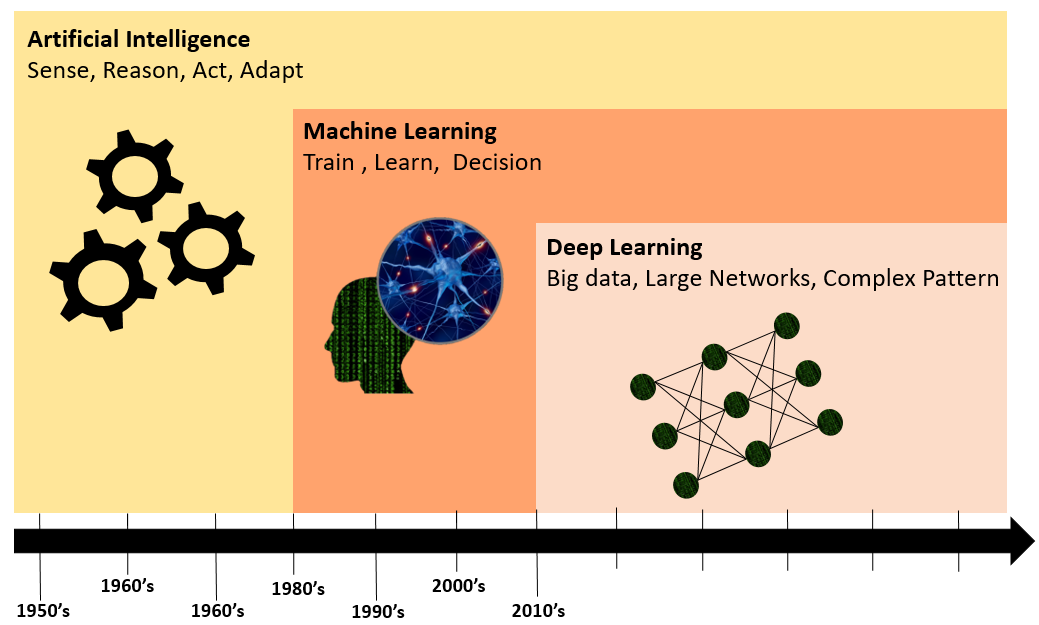
If you’re new to this field, you may be wondering what artificial intelligence is. Artificial intelligence is an alternative method of simulating human intelligence in machines that are programmed to learn in the same way as humans, mimicking human learning. The goal of an AI system is to demonstrate behaviours associated with learning, reasoning and perception of human intelligence.
Machine Learning the Subfield of AI
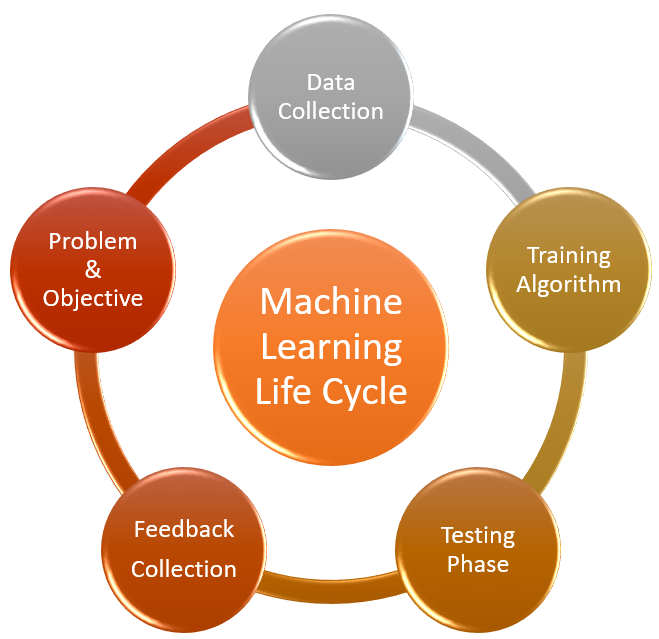
Machine learning is a subset of AI. Sometimes when we describe AI, we describe machine learning, which is the process by which AI learns. The life cycle of machine learning is as follows: you start with a problem and a goal you want to achieve; you then proceed to collect relevant data. Based on this data, you form a model based on the machine learning algorithm. After training the model, you evaluate the performance of the model by means of several test phases. You collect the feedback of natural observers on the basis of the analyzed data. Observe whether the feedback corresponds to the objectives you want to achieve. This process continues until the objective is achieved and the problem is solved.
Deep Learning vs Machine Learning
While machine learning models are gradually improving regardless of their algorithmic approaches, none of them have achieved the ultimate goal of general AI, and even narrow AI was for the most part beyond the reach of early machine learning approaches.
Thanks to Deep Learning, AI Has a Bright Future – Deep learning, which is a subset of and an evolution of machine learning, uses a hierarchical level of artificial neural networks to perform the machine learning process. The model that is trained using a deep learning strategy capable of making accurate decisions. How does deep learning algorithm works? Deep learning model is trained in such a way that, through successive analyses of data based on the similarity of its logical data structure to human perception to draw conclusions. Nowadays, Deep learning has led to many practical applications of machine learning and, by extension, the overall field of AI.
Swinburne strives to train you to become an AI researcher or engineer based on its professional learning path way and educators with a strong knowledge of AI. While the skills most in demand will vary from company to company, depending on company and industry needs, Swinburne targets the core competencies in AI engineers and researchers that are valued by all companies or industry.
Students who wish to pursue a career in AI and machine learning will acquire the required programming skills such as C++, python and Java, and become familiar with the Linux operating system and software development. In addition to the acquisition of useful software skills, the lifecycle of a student’s learning path in Swinburne involves the promotion of critical thinking for problem solving, the refinement of mathematical skills, the improvement of analytical skills for searching for important patterns in large amounts of data, and also the possession of a thorough understanding of AI algorithms.
Interested candidates can find degree programs in Swinburne that offer specific majors in AI such as Bachelor of Computer Science majoring in AI. (/courses/bachelor-of-computer-science.php
Our degree provides specialised skills and knowledge in the artificial intelligence domain which includes computer vision and pattern recognition, intelligent system, machine learning and natural language processing. By following this pathway, you will be exploring the many facet of novel techniques in building systems mimicking human-like intelligence.
Student Learning Outcomes
FYP project: Digital Room Occupancy
The Digital Room Occupancy system tracks the number of people, temperature and humidity in areas such as the recreation area, 24-hour study area, BYOD rooms and computer labs. This project is proposed in part to address a flaw in the current campus entrance system that fails to accurately estimate the number of people in the room. In addition, this project is also able to display trends based on past data.
This video is presented by Bong Jin Hong, Ng Yi, Florence Teo Hui San and Ng Chin Shu
Outreach
Bridging AI to World Environment
AI for Plant Recognition and Biodiversity – Past, Present and Future
Biodiversity is in constant decline throughout the world, mainly due to direct or indirect human activities. To protect biodiversity, people have begun building knowledge of accurate species to recognize unknown plant species. Taxonomists, botanists and other professionals determine plant species from field observations based on substantial knowledge of the species acquired through their fieldwork and studies. However, recent circumstances have seen a growing gap between supply and demand for these skills, to the extent that experts have coined the term “taxonomic impediment” to describe the distressing lack of taxonomists.
Flower, Stem or Leaf? – Recent technological advances have shown that machine learning can assist the botanist in the task of plant identification. Thanks to deep learning algorithms, we are no longer hampered by the choice of which plant organ to use to form an accurate species recognition system, but leave it to the neural network itself to make the decisions by weighting the importance of each plant organ that could best recognize a particular plant species (Lee et al., 2018). AI in plant identification has shown promising results, surpassing the human capacity to recognize more than 27,000 plant species worldwide (Goëau et al, 2013). The future direction of the research is to increase the adaptability of the machine to the real world scenario in order to be able to deal with unknown or new plant species. Automatic Plant Health Monitoring System
Automatic Plant Health Monitoring System
Plant diseases are a major threat to agricultural production, causing a severe food recession and affecting crop quality. The initial identification of the disease is usually done by visual assessment and the quality of the diagnosis depends strongly on the knowledge of human experts. Although expert consultation is one of the main means of combating plant diseases, human expertise is not easily acquired by all actors in the agricultural world and is less accessible, particularly in the case of small farms in developing countries.
New concept, perspective and methodology – Recently proposed deep learning techniques have shown a breakthrough in the deep learning algorithm to accurately identify plant diseases based on the conditional dependence between two concepts of species and diseases (Lee et al, 2020). Importantly, deep neural networks have been demonstrated to be able to effectively recognize the largest plant disease benchmark, which includes 1145 joint species-disease classes, 311 host species and 289 diseases.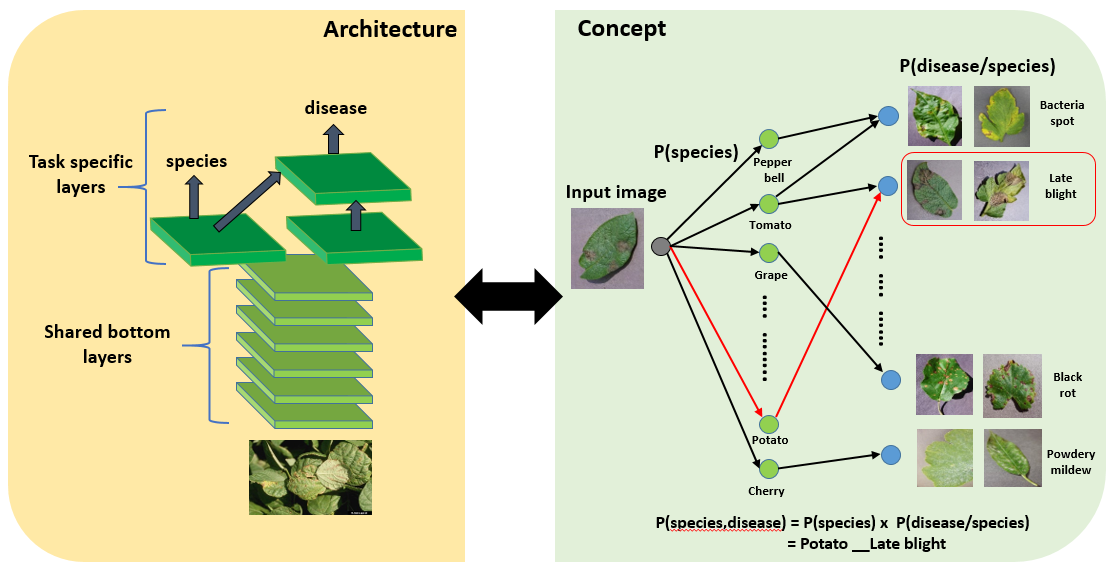
Unsupervised Classification and Anomaly Detection in Medical Imagery
The combination of medical knowledge, experience and AI algorithms have supported the advancement of patient care and the lowering of healthcare costs. Machine and deep learning methods enable the extraction of meaningful patterns that remain beyond human perception. Numerous computer-aided diagnosis and detection systems have been developed to assist in the assessment of medical imagery. However, issues are encountered when facing imbalanced, limited, and unannotated datasets. Learning from imbalanced medical datasets impairs diagnostic accuracy due to classifier bias and overfitting. Furthermore, datasets comprising of all existing abnormal classes are impossible to obtain, hence supervised algorithms would fail to generate predictions for classes devoid of training samples. Moreover, reliance on prior knowledge in the form of expert annotation and anatomical region extraction impairs scalability, as these procedures are time-consuming, computationally expensive, and limited to specific tasks.
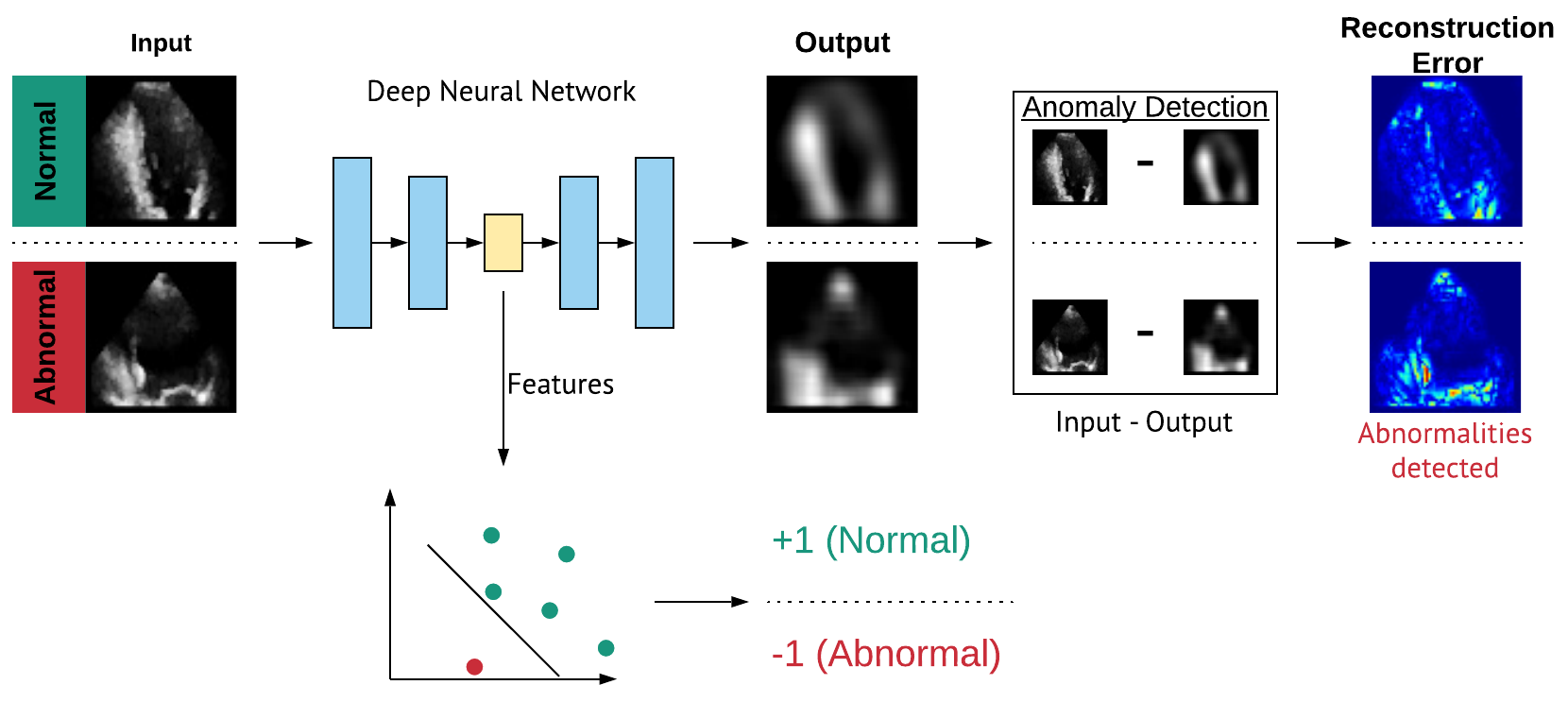
Figure 1: Unsupervised Classification and Anomaly Detection Framework
Our recent work aimed to perform classification and anomaly detection of stress echocardiograms using unsupervised deep learning techniques to discriminate between normal and abnormal videos as well as to localise wall motion abnormalities within individual frames. Deep neural networks were employed to learn visual and motion representations from multiple echocardiographic cross-sections and stress stages. Extracted features were used to discriminate between regular and irregular echocardiograms despite the absence of abnormal training samples. Reconstruction errors allowed for direct visualisation and localisation of anomalous cardiac regions, without the need for annotated training data or segmentation of structures.
Results revealed that learnt features extracted from deep neural networks trained solely on normal data can be utilised to classify abnormal stress echocardiograms with a high level of accuracy, sensitivity and specificity. In addition to that, as validated by an expert reader, reconstruction errors were capable of detecting and localising wall motion abnormalities in specific cardiac regions without prior knowledge of abnormal segments.
References
[1] Lee et al., “Multi-organ plant classification based on convolutional and recurrent neural networks.” IEEE Transactions on Image Processing 27.9 (2018): 4287-4301.
[2] Goëau, Hervé, et al. “Pl@ ntnet mobile app.” Proceedings of the 21st ACM international conference on Multimedia. 2013.
[3] Lee et al., “Conditional Multi-Task Learning for Plant Disease Identification.” International Conference of Pattern Recognition (2020) accepted, In press.
Research Activities

Professor Patrick Then (Swinburne University of Technology) and Dr Brian Chung Shiong Loh (Swinburne University of Technology) discuss the unsupervised classification and anomaly detection of stress echocardiograms with deep spatio-temporal autoencoders.
Cybersecurity is very much like the physical security that we see in our everyday life. We have many security mechanisms in place, such as locks, fences, grills, CCTVs, alarms and more, to protect us from people with bad intention. Cybersecurity involves security mechanisms to protect us in the cyber world. As we are very dependent on the internet nowadays, we also need to protect ourselves against cyberthreats and cybercriminals out in the cyber world.
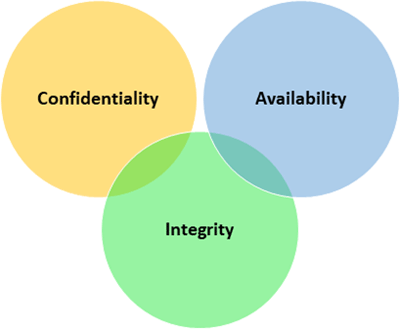
Figure 1: CIA triad
Here is a little overview of cybersecurity. There are three components that we are protecting in cybersecurity. It is the C.I.A., a very common acronym in this field. Do not confuse with the US’s Central Intelligence Agency, CIA. This acronym stands for Confidentiality, Integrity and Availability as shown in the figure above. The first aspect, Confidentiality means that whatever information that we are sending or sharing online can only be viewed and read by the person that we are sending to. For example, we will not want other people to read the message that we are sending to our friend, right? The Integrity aspect involves making sure that when we are sending or sharing any information online, no one can modify take advantage and modify this information in transit. Imagine if we are sending transfer instruction online to pay someone and the attacker get hold of this instruction and modify the recipient information to the attacker’s account before the instruction reaches the bank’s server. That will be disastrous. The last aspect, Availability aspect means that whatever services that we are accessing, such as accessing a website, making payment online, checking our emails or playing online games, should be available to us all, if not most of the time.
Cybersecurity involves upholding all these aspects. However, like any case in our real-life, we cannot have everything. Similarly, we cannot have security measures that guarantee all three aspects. If we focus on one aspect, we may need to sacrifice on another aspect. For example, we can make our system very secure to ensure confidentiality and integrity is maintained but to do that, we may need to put many restrictions that cause the availability aspect to suffer. User may only be able to access the system at a specific location or time to reduce the possibility of unauthorised access.
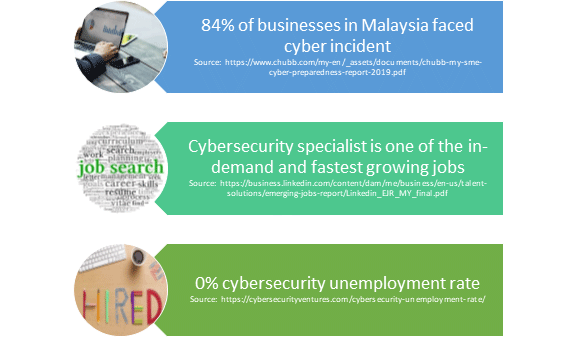
Figure 2: Cybersecurity job market
Cybersecurity is very much in demand worldwide. With businesses moving online and the COVID-19 pandemic acting as the catalyst of such movement, cybersecurity threats are becoming an issue for all these businesses. Thus, the demand for cybersecurity talent surges everywhere, even in Malaysia. Currently, the field of cybersecurity is one of the best choices one can consider in joining.
Swinburne Sarawak Programmes
Swinburne Sarawak offers the Bachelor of Computer Science programme with various majors as shown in the figure. One of the majors is the Cybersecurity major which provides in-depth knowledge about the techniques and tools used by the cybercriminals in performing malicious activities and the relevant countermeasures such as the methods, tools and skills needed to mitigate, identify and stop cybersecurity attacks. The programme leverages on the strong foundation on programming languages and networking instils upon the students at the start of their study which are very needed by those who wants to venture into the field of cybersecurity.
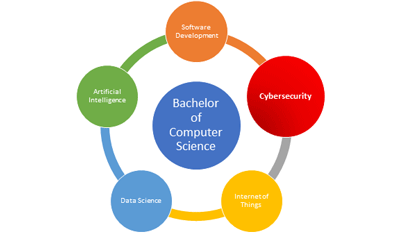
Figure 3:Majors of the Bachelor of Computer Science programme
In our dedication and commitment to providing quality education in creating industry-ready graduates, we are proud to introduce our state-of-the-art cybersecurity laboratory equipped with the ELITE SOC Simulation Lab platform that enables our students to experience the real-world defence against the cyber threat in a simulated environment. Such hands-on experience is critical for the cybersecurity students as the current industries are reluctant to hire graduates that are equipped only with knowledge of theories.
Furthermore, we will be introducing two more cybersecurity-related programmes, namely, Diploma in Computer Science majoring in Cybersecurity and Data Science, and Master of Information Technology specialising in Cybersecurity and Data Science. With the introduction of these programmes, we are becoming one of the major education providers in the field of cybersecurity in this region of the world.
Featured Learning Paths
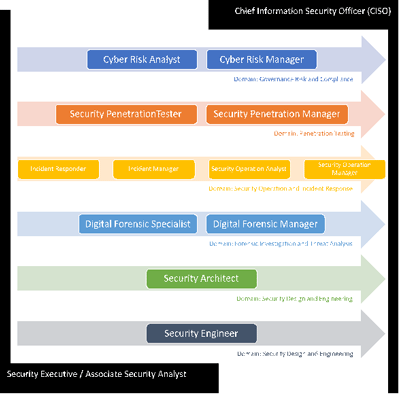
Figure 4: Cybersecurity Career Pathways. Source: HRDF’s Industrial Skills Framework (IndSF) for Digital Technology
The figure shows the various career pathways in the field of cybersecurity. The entry-level of the career pathways is the security executive or associate security analyst. Our current programme, Bachelor of Computer Science majoring in Cybersecurity prepares the students towards this role. Our programme equips the students with the knowledge and skills to understand the various techniques and tools to perform cyber-attacks, identify the common security breaches using various tools, perform vulnerability and risk assessment, and execute digital forensic investigations. The students can pursue a specialisation in various domains as shown in the figure in their career development. We are currently developing advance units which enable our students to venture into specialisation into a specific domain such as penetration testing, malware analysis and security operation and incident response.

Figure 5:Cybersecurity domains
Our near future plan is to extend our advance units in the form of short courses for those who are interested to pursue a specialisation in a specific domain. The courses will be conducted on campus, with the participants having access to our cybersecurity lab. These courses are open to anyone who are interested and not limited to our students or alumni only.
In Swinburne University of Technology Sarawak Campus, our programmes focus on helping our students to achieve the learning outcomes through real-life learning with our extensive linkage with the industries, state-of-the-art laboratories and facilities and having membership with various academy such as Tecforte, AWS academy, CISCO and Cloudera.
During the COVID-19 pandemic, we continue to strive to provide quality education to our students and to ensure that our students are still achieving their learning outcomes despite the lack of face-to-face, on-campus learning. Below is the recording of one of our webinar series on students’ experience in AI and cybersecurity. The testimony from our cybersecurity-major students’ experience during this pandemic can be viewed.
Webinar recording: https://www.facebook.com/swinburnesarawak/videos/372177170413996/
Outreach and Research Activities
Outreach
In pursue of the advancement and excellence in the field of cybersecurity, we are dedicated in our research and development efforts. One area of focus by our researchers is in the detection of phishing websites. There are many techniques deployed by the phishers with various mediums and vectors (Chiew et al., 2018b; Yong et al., 2019) to phish for valuable information from their victims. The understanding of these phishing techniques is crucial for the identification of gaps and areas where the countermeasures failed to address. Also, such a systematic review of the phishing techniques gives awareness to the readers of the danger of these phishing attacks.
Many efforts to mitigate and detect these phishing attacks were performed. This effort resulted in the proposal of detection algorithms that leverage on the website favicon (Chiew et al., 2018a), Cumulative Distribution Function gradient (Chiew et al., 2019) and Graph-Theoretic approach (Tan et al., 2020).
Another area of interest is the detection insider threat which is a challenging task in the cybersecurity field. Many countermeasures are deployed to prevent cyber-attacks from outside the network, but these countermeasures fail to detect any attack coming from within the network. This is because the defences are located at the border of the internal and external network and will not be triggered if there are any insider attacks. Currently, the research is leveraging on the use of deep learning, prior knowledge, and various data sources in detecting such attacks.
References
Chiew, K. L., Choo, J. S. F., Sze, S. N., & Yong, K. S. (2018a). Leverage website favicon to detect phishing websites. Security and Communication Networks, 2018.
Chiew, K. L., Tan, C. L., Wong, K., Yong, K. S., & Tiong, W. K. (2019). A new hybrid ensemble feature selection framework for machine learning-based phishing detection system. Information Sciences, 484, 153-166.
Chiew, K. L., Yong, K. S. C., & Tan, C. L. (2018b). A survey of phishing attacks: Their types, vectors and technical approaches. Expert Systems with Applications, 106, 1-20.
Tan, C. L., Chiew, K. L., Yong, K. S., Abdullah, J., & Sebastian, Y. (2020). A Graph-Theoretic Approach for the Detection of Phishing Webpages. Computers & Security, 101793.
Yong, K. S., Chiew, K. L., & Tan, C. L. (2019, June). A survey of the QR code phishing: the current attacks and countermeasures. In 2019 7th International Conference on Smart Computing & Communications (ICSCC) (pp. 1-5). IEEE.
Press Articles:
Article coverage in other press:
Recording:
Link: Play recording
Password: 7FbwECWm
Upcoming newspaper article on Sept 30.
Data Science involves multiple disciplines. Therefore, data scientists are analytical data experts equipped with an array of technical and non-technical competencies, including statistics, programming languages, databases, machines learning, teamwork and communication skills. They use their know-how and abilities to collect, analyse and interpret large data sets, and create new tools or processes to help solve analytically complex problems in the real-world.
Data scientists are also big data wranglers. They are often full of curiosity to discover underlying patterns and trends from massive amounts of data and develop methods to extract meaningful information for decision making. They use their skills in both technology and social science to analyse and interpret data and transform data insights into actionable recommendations that solve business challenges. They engage lots advanced analytics technologies in finding solutions and communicate results to the stakeholders.
Data scientists are highly sought after especially in the era of big data. They require not only technical skills in statistics and programming but also business sense and good communication skills. They often exist in business settings and are charged with communicating complex ideas and making data-driven organisational decisions. As a result, they need to be effective leaders, engaged team members, clear communicators as well as high-level analytical thinkers.
There are six common steps to break into the field of data science: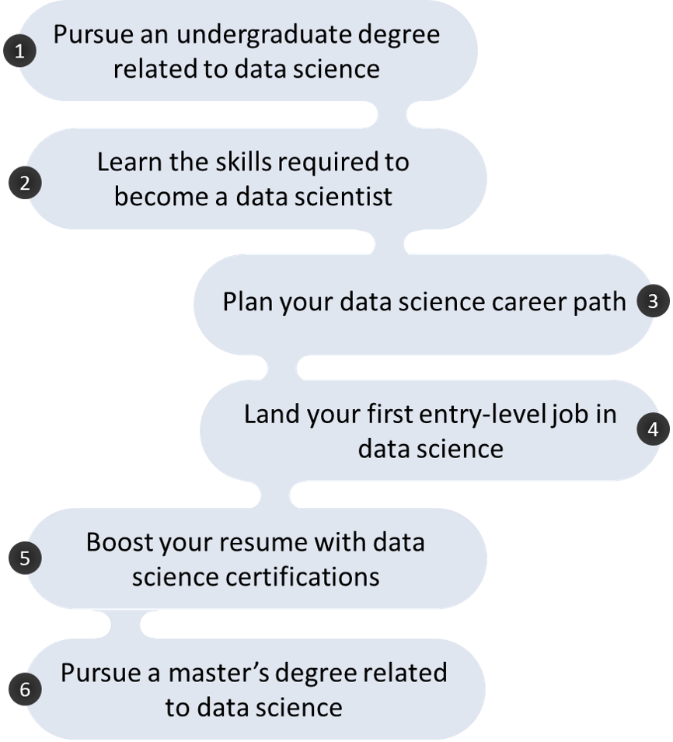
Step 1: Pursuing an undergraduate degree related to data science
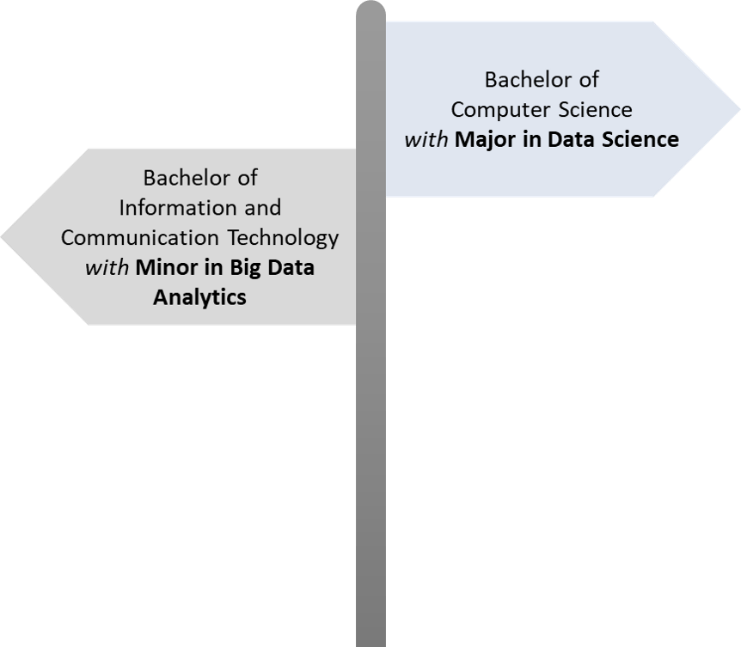
Earning an undergraduate degree is the first step to becoming a data scientist. Swinburne Sarawak is offering two undergraduate degree options for students interested in data science field. These options are designed to equip students with the skills required to become a data scientist (Step 2) and to meet the demand of data scientists with different specialisations (Step 3).
Before landing your first entry-level job in the field of data science (Step 4), you may also consider earning professional data scientist certifications (Step 5) or enrolling into a master’s degree in data science (Step 6).
Step 2: Learn the skills required to become a data scientist
Various industries and sectors are heavily reliant on data scientists such as agriculture, healthcare, marketing optimization and manufacturing. Data scientists utilise a combination of skills to support organisations in making objective decisions. The most competent data scientists are familiar with programming languages such as Python and R, as well as machine learning techniques, data visualisation and Big Data platforms. The diagram below illustrates the data science skills that can be acquired by students upon completion of their studies (Step 1) at Swinburne Sarawak.
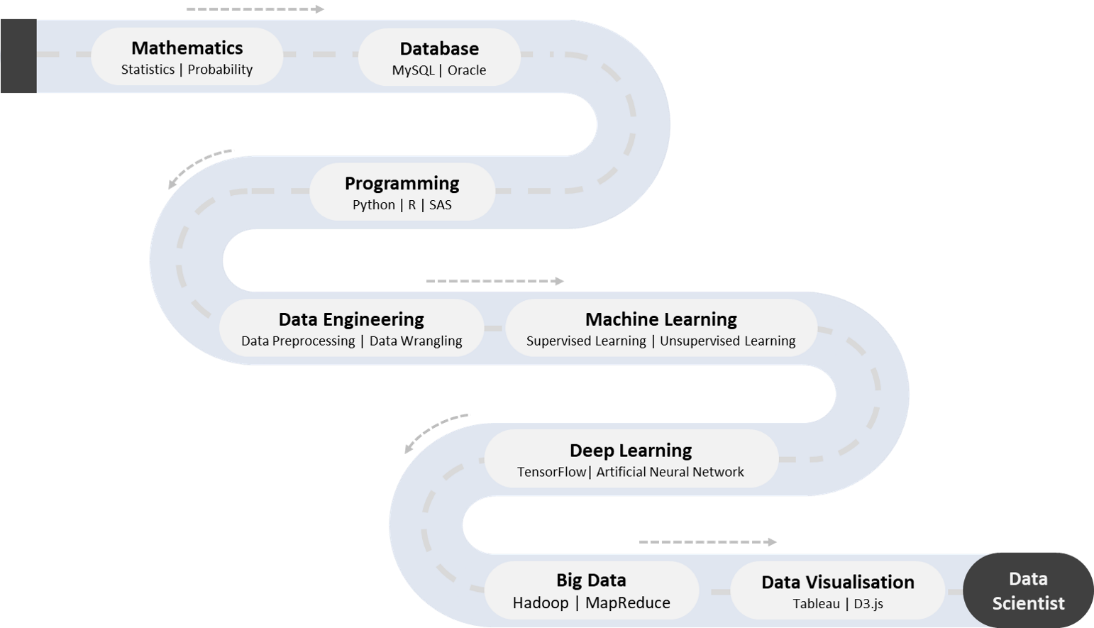
It is also important for students to plan their data science career path (Step 3) in order to equip themselves with the knowledge and skills necessary to get an entry level data science job (Step 4).
Step 3: Plan your data science career path
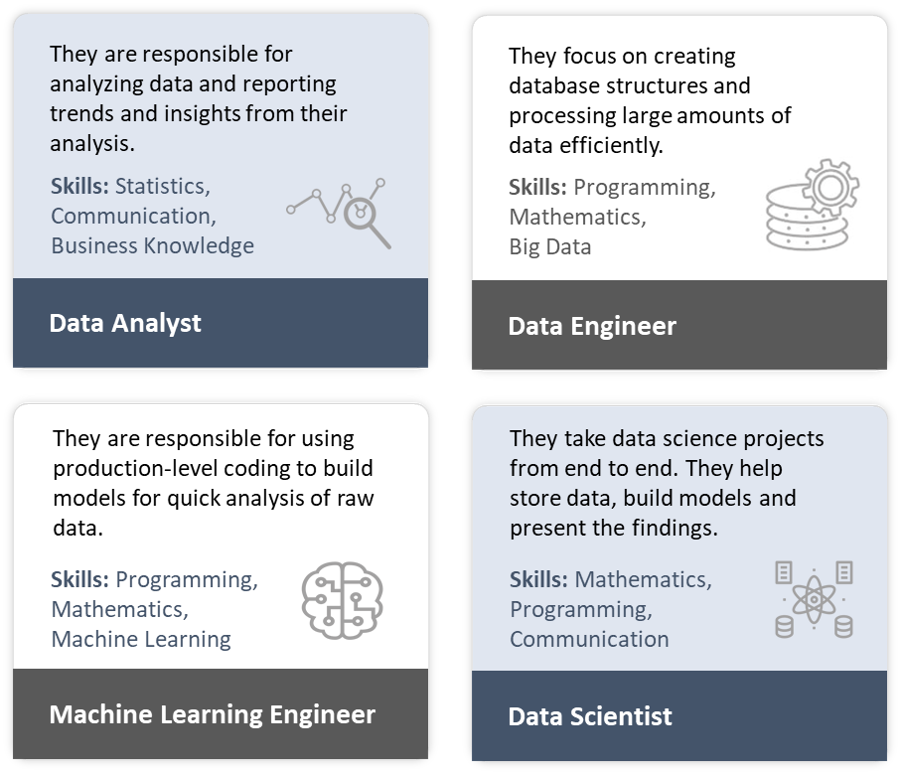
Data science field offers a variety of highly desirable career paths. Those who wish to venture into data science field should be knowledgeable of the different career paths available and choose the path that allow them to shine best. The diagram below compares the different skillsets needed for the top careers in data science field: data analyst, data engineer, machine learning engineer and data scientist.
Step 4: Land your first entry-level job in data science
Once you have acquired your specialization in data science, it is time to create an online portfolio to showcase your skills, experience and abilities to prospective employers. You may not have the title ‘data scientist’ for your first data science job; however, you may want to consider a company where you can develop your professional skills. You will learn ways to work on a project as a team and find the best practices that will help you in your career progression.
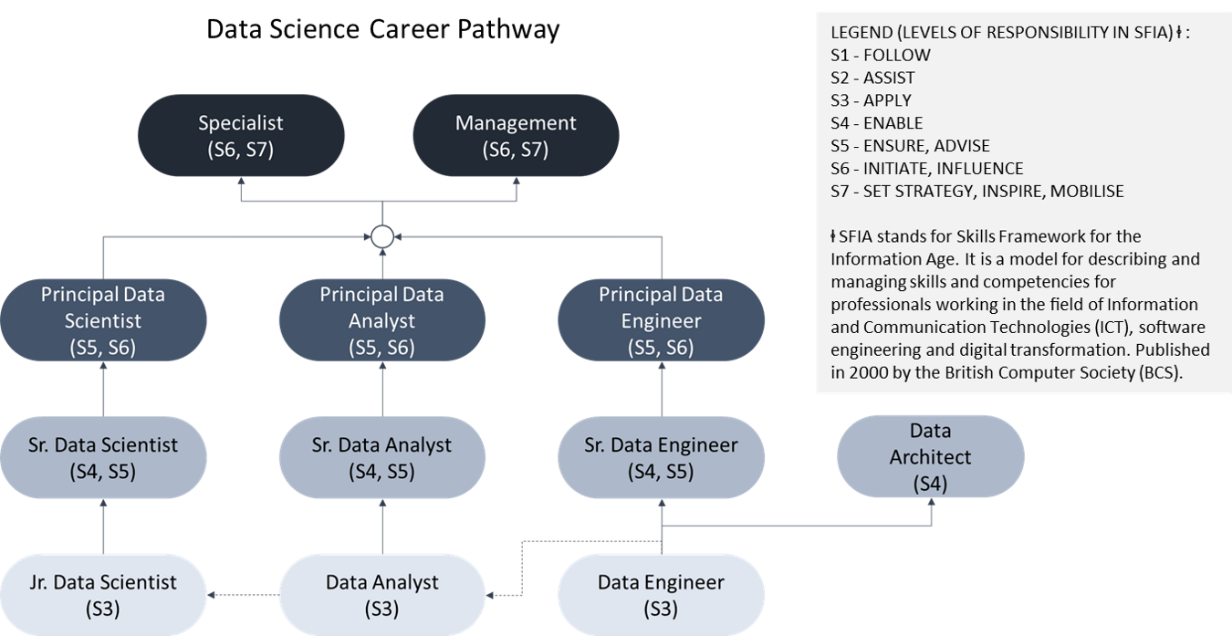
Source: HRDF’s Industrial Skills Framework (IndSF) for Digital Technology
You should also persevere in acquiring new data science skills and learning latest data analytics tools to boost your resume (Step 5) or consider pursuing a master’s degree in data science field (Step 6).
Step 5: Boost your resume with data science certifications
Upon completion of undergraduate studies, graduates may choose to either pursue for specialised professional certifications or a postgraduate master’s degree (Step 6). The Undergraduate Minor of Big Data Analytics and Major in Data Science at Swinburne Sarawak (Step 2) comprised of units of study designed to help students prepare for data science professional certifications, including:

Industry recognised certifications can enrich your resume and potentially qualify you for more advanced job positions. Other common data science certifications include:
Step 6: Pursue a master’s degree related to data science
Is a master’s degree necessary to land a job as a data scientist? It solely depends on the job requirements. An undergraduate degree is often required to become a data scientist; however, having a master’s degree or PhD allows you to enter the profession at a higher level. According to Burtch Works (2019), over 90% of data scientists have a master’s degree or PhD. An earlier study by the Quant Crunch (2017) reported that 39% of data scientists and advanced analysts require a master’s degree or PhD.
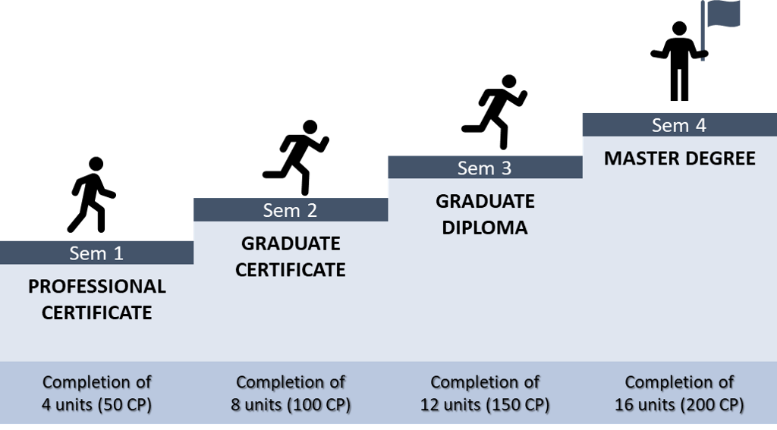
Swinburne University is offering Master of Information Technology (MIT) course starting 2021. The course provides advanced skills and introduce state-of-the-art techniques used in the design and construction of IT solutions, as well as the research skills needed to assess the effectiveness of a solution or technology. Upon completion of this course, students will gain specialized skills and become capable of working with IT solutions at an advance level. The MIT course offered provides two options of specialisations which are Data Science and Cybersecurity.
The MIT course takes four semesters of full-time study or eight semesters of part time study and require the successful completion of 16 units (200 CP). Students can exit the course early and apply to graduate with Graduate Certification (100 CP) or Graduate Diploma (150 CP).
Data Science is evolving quickly and blooming in different fields of businesses and industries. Organisations are increasingly recognizing the value of using data to improve decision making in their businesses. With the emergence of Big Data and Artificial Intelligence, the demand for data science skills is growing exponentially. Data professionals with different level of responsibilities are in high demand especially in top companies like Google, Facebook and Huawei and in Federal corporation as well as Government sectors. However, there aren’t a lot of people possessing a combination of various skillsets needed ranging from scientific background, computational skills and analytic skills. Rapid proliferation of data and analytics demand makes data scientist one of the highest paying jobs in the IT industry.
Data is the new oil. With the advancements in computational capabilities, a massive amount of data is collected, processed and stored every second to generate proper data-driven decisions. Here are a few examples of data science use cases that have changed our way of life:
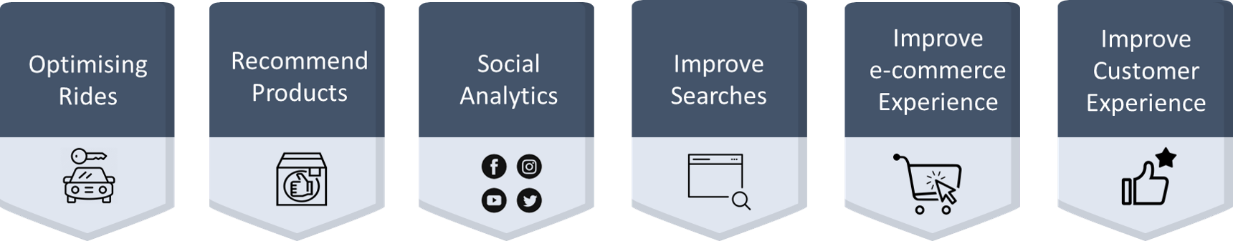
Swinburne Sarawak has conducted a series of webinar, outreach and research activities primarily to create awareness regarding the power of data science both internally and externally.
 Webinar |Transforming Data into Values |  Winners | Innovate Malaysia Design Competition 2020 (Link) |
 Workshop | Python Basics for Newbies for secondary schools |  Research | SAS to power Smart City plans with local analytics talent (Link) |